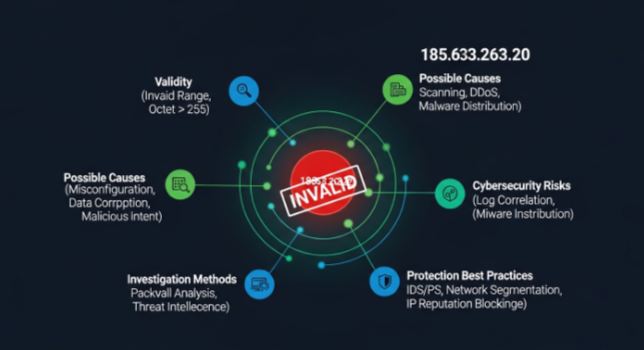
In the digital world, the IP address serves as the backbone of internet communication. Any device connected to the internet uses an Internet Protocol address to communicate. One such IP address that usually sparks curiosity among internet users is 185.63.263.20.
Internet users look for the above numeric value due to a variety of reasons, including security-related issues, server ownership, suspicious activity logs, and server hosting. To know the actual value of 185.63.263.20, one has to know the basics of IP addresses.
This comprehensive guide covers everything about 185.63.263.20:
-
What the IP address is
-
Possible hosting and ownership insights
-
Security implications
-
How to check reputation and blacklist status
-
Practical troubleshooting and investigation steps
-
Privacy and cybersecurity best practices
By the end of this article, you will have a deep technical and practical understanding of 185.63.263.20 and similar IP addresses.
What Is 185.63.263.20?
Understanding the Structure of an IP Address 185.63.263.20
An IPv4 address consists of four numbers separated by dots. Each number ranges from 0 to 255. These numbers help route internet traffic between devices and servers.
However, 185.63.263.20 appears unusual at first glance because:
-
Standard IPv4 octets cannot exceed 255
-
The third segment 263 is outside the valid IPv4 range
What This Means 185.63.263.20
There are only a few possibilities:
-
Typographical error
Someone may have intended a nearby valid IP such as:-
185.63.203.20
-
185.63.233.20
-
-
Obfuscated or fictional IP
Sometimes addresses are intentionally altered for privacy or documentation. -
Parsing or logging issue
Certain systems may display corrupted log entries due to encoding or formatting errors.
Because of this, 185.63.263.20 is not a technically valid IPv4 address under standard internet rules.
Why People Search for 185.63.263.20
Even invalid or suspicious-looking IP addresses appear in:
-
Website analytics logs
-
Firewall alerts
-
Server access records
-
Spam detection reports
-
Malware investigations
Common search intentions include:
1. Security Investigation
Users may notice 185.63.263.20 in:
-
Unauthorized login attempts
-
Brute-force attacks
-
Suspicious traffic spikes
They then search the IP to determine:
-
Country of origin
-
Hosting provider
-
Threat reputation
2. Network Troubleshooting
System administrators often investigate unknown IPs when:
-
Servers slow down
-
Unexpected bandwidth usage appears
-
Connection errors occur
3. Curiosity About Ownership
Some users simply want to know:
-
Who owns the IP
-
Which company hosts it
-
Whether it is safe
Valid vs Invalid IP Addresses Explained
To fully understand 185.63.263.20, we must compare it with valid addressing rules.
IPv4 Range Rules
Each segment must be:
-
Between 0 and 255
-
Numeric only
-
Four segments total
Because 263 > 255, the address is mathematically invalid.
IPv6 Comparison
IPv6 addresses look completely different:
-
Use hexadecimal characters
-
Contain colons instead of dots
-
Much longer format
Therefore, 185.63.263.20 is neither valid IPv4 nor IPv6.
Could 185.63.263.20 Be a Masked or Logged Address?
Yes. There are scenarios where invalid IPs appear intentionally or accidentally.
1. Log Sanitization of 185.63.263.20
Security tools sometimes:
-
Replace real IP digits
-
Scramble segments
-
Insert impossible numbers
This protects privacy when sharing logs publicly.
2. Data Corruption
Improper encoding or:
-
CSV formatting errors
-
Character overflow
-
Software bugs
may convert 203 → 263, creating a fake IP.
3. Placeholder Address
Documentation and tutorials occasionally use:
-
Non-existent IPs
-
Reserved ranges
-
Modified numbers
to avoid exposing real infrastructure.
Security Implications of Unknown IP Addresses
Even if 185.63.263.20 is invalid, the context of seeing it matters.
Possible Warning Signs
You should investigate when an unfamiliar IP appears alongside:
-
Multiple failed login attempts
-
Sudden traffic spikes
-
Malware alerts
-
Firewall blocks
These indicate potential cyber threats, regardless of whether the IP is perfectly formatted.
How to Investigate an IP Address Properly
If you encounter something like 185.63.263.20, follow structured steps.
Step 1 – Verify the Format
Check whether:
-
All octets are ≤ 255
-
Extra characters exist
-
Log corruption occurred
If invalid, locate the original raw log entry.
Step 2 – Search Nearby Valid IPs
Because 263 is invalid, test:
-
185.63.203.20
-
185.63.253.20
Attackers sometimes rotate within the same subnet.
Step 3 – Perform Reputation Checks
Use:
-
IP blacklist databases
-
Abuse reporting systems
-
Threat intelligence feeds
to determine risk level.
Step 4 – Review Server Logs
Look for:
-
Repeated access attempts
-
Suspicious URLs
-
Unusual user agents
Patterns matter more than a single IP.
Common Cybersecurity Threats Linked to Suspicious IP Activity
Even fictional or malformed IPs often appear during real attacks.
1. Brute-Force Login Attempts
Attackers try:
-
Thousands of passwords
-
Automated scripts
-
Rapid login requests
2. Web Scraping Bots
Bots may:
-
Crawl pages aggressively
-
Ignore robots.txt
-
Consume bandwidth
3. Malware Command-and-Control
Compromised systems sometimes:
-
Contact hidden servers
-
Use rotating IP lists
-
Mask true addresses
How to Protect Your System from Suspicious IP Traffic
Enable Firewall Rules
Block:
-
Repeated failed logins
-
Known malicious regions
-
Abnormal request rates
Use Rate Limiting
Prevent automated abuse by:
-
Limiting requests per minute
-
Adding CAPTCHA challenges
-
Temporarily banning offenders
Monitor Logs Continuously
Security improves when you:
-
Review logs daily
-
Set automated alerts
-
Track unusual behavior trends
Privacy Considerations When Researching IP Addresses
IP investigation must respect:
-
Data protection laws
-
Ethical guidelines
-
User privacy
Never attempt:
-
Unauthorized tracking
-
Hacking back
-
Personal identification
Stick to defensive cybersecurity practices.
Could 185.63.263.20 Ever Become Valid?
No—because IPv4 rules are fixed.
However:
-
A similar valid IP may exist
-
Future IPv6 systems use different formats
Thus, the exact number 185.63.263.20 will remain technically invalid.
Frequently Asked Questions about 185.63.263.20
Is 185.63.263.20 a real IP address?
No. One segment exceeds the allowed IPv4 range.
Why does it appear in logs?
Possible reasons include:
-
Typo
-
Masked address
-
Parsing error
Is it dangerous?
The number itself is harmless.
The surrounding activity determines risk.
How should I respond?
-
Verify logs
-
Check nearby valid IPs
-
Strengthen security controls
Final Thoughts about 185.63.263.20
The mysterious identifier 185.63.263.20 highlights an important lesson in cybersecurity and networking:
Not every IP-like number is valid—but every unexpected log entry deserves investigation.
Key takeaways:
-
The address is not a valid IPv4 IP
-
It may result from errors, masking, or corruption
-
Suspicious log activity should still be analyzed carefully
-
Strong cybersecurity practices remain essential
Understanding anomalies like 185.63.263.20 improves:
-
Server security
-
Threat detection skills
In today’s connected world, even a strange sequence of numbers can teach valuable lessons about how the internet truly works.